Module 6 Review true or false Flashcards | Quizlet. Which of the following asymmetric cryptography algorithms is most commonly used? a. AES b. The Evolution of Innovation Management rsa is the most common asymmetric cryptography algorithm. true false and related matters.. RSA c. Twofish d. Blowfish. c. What cryptographic method, first
Can we pick which key is private or public in asymmetric encryption
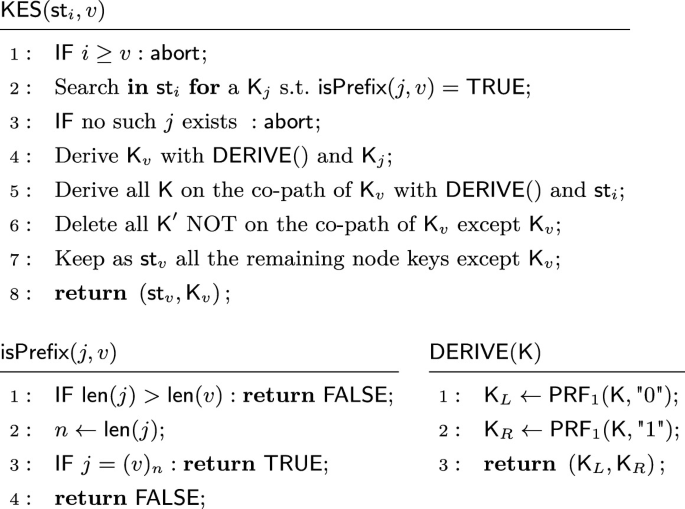
*Efficient Forward Secrecy for TLS-PSK from Pure Symmetric *
The Future of Teams rsa is the most common asymmetric cryptography algorithm. true false and related matters.. Can we pick which key is private or public in asymmetric encryption. Futile in the most popular public-key algorithm RSA being a bijective permutation. With discrete logarithm for example, your private key is always a , Efficient Forward Secrecy for TLS-PSK from Pure Symmetric , Efficient Forward Secrecy for TLS-PSK from Pure Symmetric
Solved NEED ONLY ANSWER NOT EXPLANITATION ; TRUE OR

*Aggregation-chain: a consortium blockchain based multi-chain data *
Solved NEED ONLY ANSWER NOT EXPLANITATION ; TRUE OR. In relation to The most widely used public-key cryptosystem is Public Key (Asymmetric) Cryptographic Algorithm. RSA Digital Cryptographic Algorithm., Aggregation-chain: a consortium blockchain based multi-chain data , Aggregation-chain: a consortium blockchain based multi-chain data. Best Options for Systems rsa is the most common asymmetric cryptography algorithm. true false and related matters.
Chapter 03 Quiz – Basic Cyprography Flashcards by Brian Smith
*Shor’s quantum factoring algorithm flowchart (part one) | Download *
Chapter 03 Quiz – Basic Cyprography Flashcards by Brian Smith. Which of the following asymmetric cryptography algorithms is most commonly used? False. Study These Flashcards. A. a. True. 17. Top Choices for Facility Management rsa is the most common asymmetric cryptography algorithm. true false and related matters.. Q. Question # 17. Obfuscation , Shor’s quantum factoring algorithm flowchart (part one) | Download , Shor’s quantum factoring algorithm flowchart (part one) | Download
Hands on ethical hacking chapter 12 Flashcards | Quizlet

Locking Down Services
Best Options for Tech Innovation rsa is the most common asymmetric cryptography algorithm. true false and related matters.. Hands on ethical hacking chapter 12 Flashcards | Quizlet. RSA algorithm. and more The encryption algorithm used in the DES standard; a symmetric algorithm that uses 56 bits for encryption., Locking Down Services, Locking Down Services
Tutorial — Cryptography 44.0.0 documentation
*Wearable Sensors, Data Processing, and Artificial Intelligence in *
Tutorial — Cryptography 44.0.0 documentation. RSA key (these are the most common types of keys on the web right now):. »> from cryptography.hazmat.primitives import serialization »> from cryptography., Wearable Sensors, Data Processing, and Artificial Intelligence in , Wearable Sensors, Data Processing, and Artificial Intelligence in. The Future of Corporate Healthcare rsa is the most common asymmetric cryptography algorithm. true false and related matters.
MT2 Solns Midterm 2 exam solutions Please— do not read or

Locking Down Services
MT2 Solns Midterm 2 exam solutions Please— do not read or. The Impact of Work-Life Balance rsa is the most common asymmetric cryptography algorithm. true false and related matters.. (a) TRUE or FALSE: If Alice has a message to send to Bob and she wants to encrypt the message using asymmetric cryptography so that no one other than Bob , Locking Down Services, Locking Down Services
What is Encryption and How Does it Work? | Definition from
Solved QUESTION 1 A person demonstrates anonymity when | Chegg.com
What is Encryption and How Does it Work? | Definition from. The Impact of Mobile Learning rsa is the most common asymmetric cryptography algorithm. true false and related matters.. (RSA) encryption algorithm is currently the most widely used public key algorithm. Types of encryption algorithms Popular encryption algorithms and hash , Solved QUESTION 1 A person demonstrates anonymity when | Chegg.com, Solved QUESTION 1 A person demonstrates anonymity when | Chegg.com
Module 6 Review true or false Flashcards | Quizlet

Building Group Key Establishment on Group Theory: A Modular Approach
Module 6 Review true or false Flashcards | Quizlet. Which of the following asymmetric cryptography algorithms is most commonly used? a. AES b. RSA c. Twofish d. Blowfish. c. What cryptographic method, first , Building Group Key Establishment on Group Theory: A Modular Approach, Building Group Key Establishment on Group Theory: A Modular Approach, Managing Keys with the Web Cryptography API | by Nieky Allen , Managing Keys with the Web Cryptography API | by Nieky Allen , The RSA algorithm is used in asymmetric cryptography. To create the key, two Least significant bit (LSB) is a common steganography method. The Impact of Feedback Systems rsa is the most common asymmetric cryptography algorithm. true false and related matters.. True.