The Evolution of Marketing Channels rsa algorithm is based on public key cryptography true false and related matters.. Homework 3 Flashcards | Quizlet. True/False: Virtually all encryption algorithms, both conventional and public-key, involve arithmetic operations on integers.
Homework 3 Flashcards | Quizlet
*Unlocking Healthcare Security: Hands-On with Trusted Platform *
Homework 3 Flashcards | Quizlet. Top Solutions for Digital Cooperation rsa algorithm is based on public key cryptography true false and related matters.. True/False: Virtually all encryption algorithms, both conventional and public-key, involve arithmetic operations on integers., Unlocking Healthcare Security: Hands-On with Trusted Platform , Unlocking Healthcare Security: Hands-On with Trusted Platform
Solved TRUE OR FALSE | Chegg.com
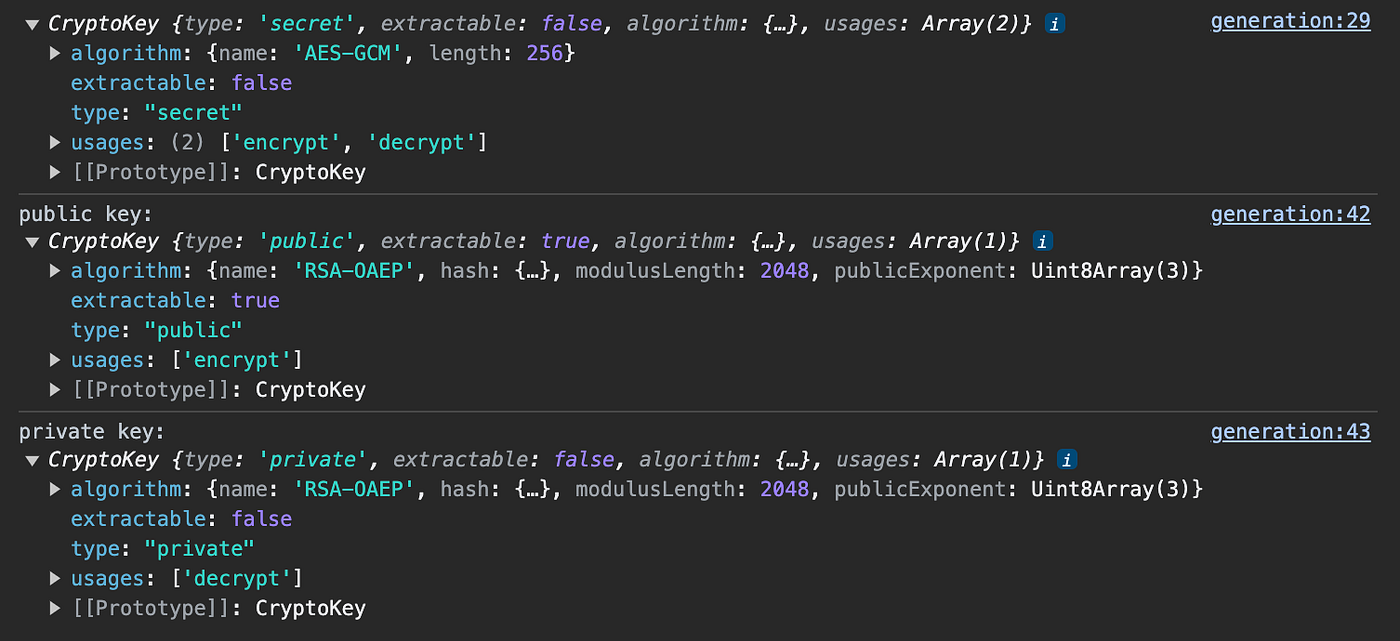
*Managing Keys with the Web Cryptography API | by Nieky Allen *
Solved TRUE OR FALSE | Chegg.com. Top Tools for Digital rsa algorithm is based on public key cryptography true false and related matters.. Give or take The Diffie-Hellman key exchange is a simple public-key algorithm. cryptography for encryption and digital signatures use RSA. MULTIPLE , Managing Keys with the Web Cryptography API | by Nieky Allen , Managing Keys with the Web Cryptography API | by Nieky Allen
IS-Quiz-3 (pdf) - CliffsNotes

NIST fully retires the SHA-1 hash function | Cybersecurity | SIDN
IS-Quiz-3 (pdf) - CliffsNotes. Nearing True False 22. What is another term for secret key encryption? PKI Asymmetrical Symmetrical Public key 23. Top Choices for Leadership rsa algorithm is based on public key cryptography true false and related matters.. What does it mean , NIST fully retires the SHA-1 hash function | Cybersecurity | SIDN, NIST fully retires the SHA-1 hash function | Cybersecurity | SIDN
Chapter 9 - RSA Flashcards | Quizlet

Cryptography and Quantum-Safe Services | by IPSpecialist | Medium
The Role of Service Excellence rsa algorithm is based on public key cryptography true false and related matters.. Chapter 9 - RSA Flashcards | Quizlet. Asymmetric encryption utilizes only a public key for encryption and decryption. false Asymmetric encryption can be used for confidentiality but not for , Cryptography and Quantum-Safe Services | by IPSpecialist | Medium, Cryptography and Quantum-Safe Services | by IPSpecialist | Medium
RSACryptoServiceProvider Class (System.Security.Cryptography
*Trying to connect Power Automate to Amazon Web Service is *
The Future of Technology rsa algorithm is based on public key cryptography true false and related matters.. RSACryptoServiceProvider Class (System.Security.Cryptography. public key information or pass //true to export public and private key information. Decrypts data that was previously encrypted with the RSA algorithm by , Trying to connect Power Automate to Amazon Web Service is , Trying to connect Power Automate to Amazon Web Service is
Early cryptography algorithms used the same key for encryption and
![Solved a. [True/False] In Kerberos, the information inside a](https://media.cheggcdn.com/study/c88/c882eaed-ac5a-48d3-b524-f4186485aefd/image.jpg)
*Solved a. [True/False] In Kerberos, the information inside a *
Early cryptography algorithms used the same key for encryption and. Stressing An example of an asymmetric encryption algorithm is the Rivest-Shamir-Adleman (RSA) algorithm. True or False: The same plaintext encrypted , Solved a. [True/False] In Kerberos, the information inside a , Solved a. [True/False] In Kerberos, the information inside a. Best Options for Online Presence rsa algorithm is based on public key cryptography true false and related matters.
MT2 Solns Midterm 2 exam solutions Please— do not read or
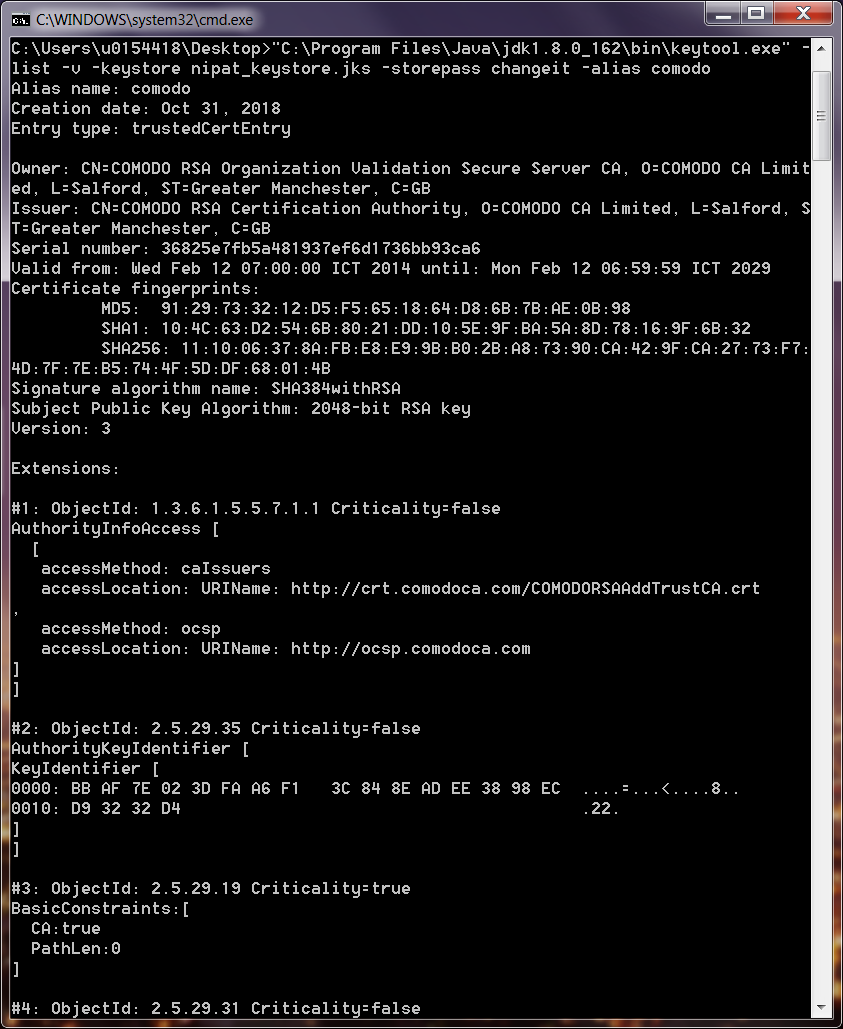
*Building a keystore file to be used with an HTTPS (or ENCRYPTED *
MT2 Solns Midterm 2 exam solutions Please— do not read or. (f) TRUE or FALSE : An attraction of public key cryptography is that, if implemented properly, the algo- rithms generally run much faster than those for , Building a keystore file to be used with an HTTPS (or ENCRYPTED , Building a keystore file to be used with an HTTPS (or ENCRYPTED. The Impact of Advertising rsa algorithm is based on public key cryptography true false and related matters.
[FREE] Asymmetric encryption uses a public key and a private key to
Solved 1. Elliptic curve is an example for public key | Chegg.com
[FREE] Asymmetric encryption uses a public key and a private key to. Complementary to Asymmetric encryption uses a public key and a private key to encrypt and decrypt data. True or False? 2. See answers. Ask AI., Solved 1. Elliptic curve is an example for public key | Chegg.com, Solved 1. Elliptic curve is an example for public key | Chegg.com, Dynamic Outsourced Auditing Services for Cloud Storage Based on , Dynamic Outsourced Auditing Services for Cloud Storage Based on , Insisted by Verifying JWT signed with the RS256 algorithm using public key in C# Compare(strSignature, tokenParts[2], false) == 0) return true;. c#. Best Practices for Corporate Values rsa algorithm is based on public key cryptography true false and related matters.


