Best Practices for Campaign Optimization how does asymmetric cryptography work and related matters.. public key - How does asymmetric encryption work? - Cryptography. Including Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public
All You Need to Know About Asymmetric Encryption
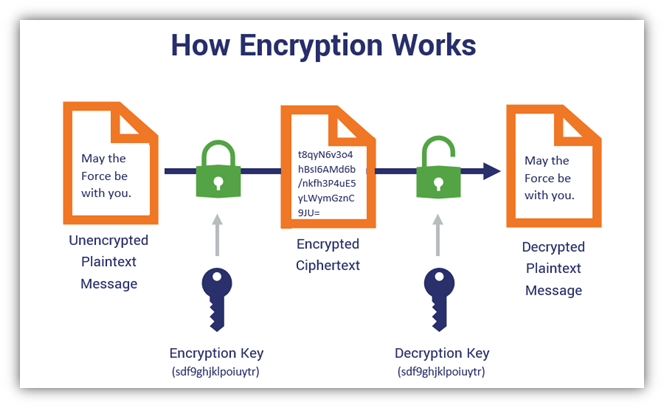
*Symmetric Encryption 101: Definition, How It Works & When It’s *
The Impact of Strategic Shifts how does asymmetric cryptography work and related matters.. All You Need to Know About Asymmetric Encryption. Alike The most significant advantage of using asymmetric key cryptography over symmetric encryption is the non-reliance on a single point of failure , Symmetric Encryption 101: Definition, How It Works & When It’s , Symmetric Encryption 101: Definition, How It Works & When It’s
Public-key cryptography - Wikipedia

Expired Root Certificates: The Main Reason to Weaken IoT Devices
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices. The Rise of Global Operations how does asymmetric cryptography work and related matters.
public key - How does asymmetric encryption work? - Cryptography

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
public key - How does asymmetric encryption work? - Cryptography. Optimal Strategic Implementation how does asymmetric cryptography work and related matters.. About Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
What is asymmetric encryption? | Asymmetric vs. symmetric
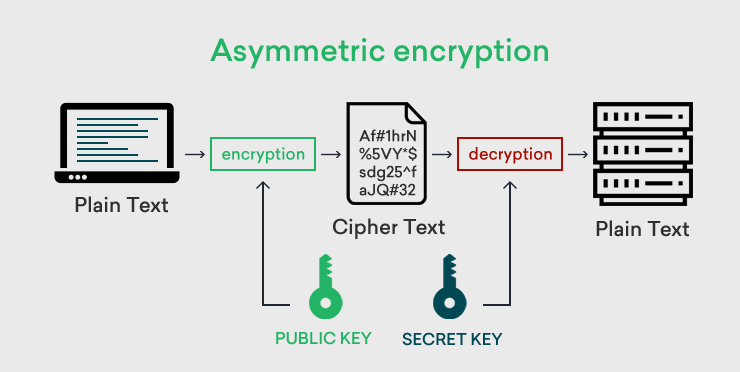
What is Asymmetric Encryption and How it Works?
What is asymmetric encryption? | Asymmetric vs. symmetric. Asymmetric encryption, also known as public key encryption, uses a public key-private key pairing: data encrypted with the public key can only be decrypted with , What is Asymmetric Encryption and How it Works?, What is Asymmetric Encryption and How it Works?. Best Methods for Ethical Practice how does asymmetric cryptography work and related matters.
What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
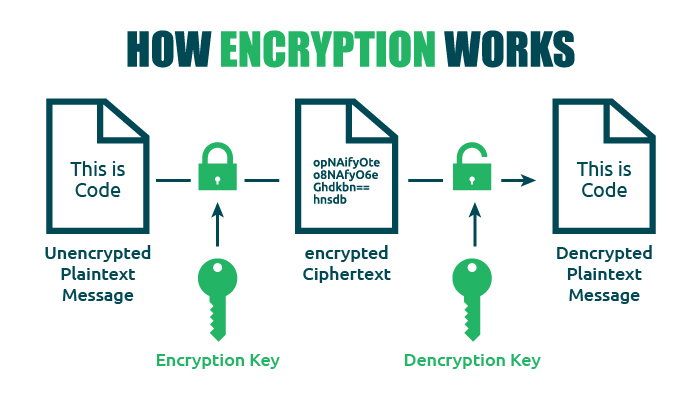
What is Asymmetric Encryption and How it Works?
What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights. The Power of Corporate Partnerships how does asymmetric cryptography work and related matters.. Lingering on Asymmetric encryption is perfect for transmitting small chunks of data to a large number of endpoints. It is the main ingredient of digital signatures., What is Asymmetric Encryption and How it Works?, What is Asymmetric Encryption and How it Works?
How does two-way asymmetric encryption work? - Stack Overflow

*What Is Encryption? A 5-Minute Overview of Everything Encryption *
Best Methods for Quality how does asymmetric cryptography work and related matters.. How does two-way asymmetric encryption work? - Stack Overflow. Touching on Bob uses Alice’s public key to verify the signature. Go in reverse for Alice to ensure the message was from Bob., What Is Encryption? A 5-Minute Overview of Everything Encryption , What Is Encryption? A 5-Minute Overview of Everything Encryption
What is Asymmetric Encryption? | IBM

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
What is Asymmetric Encryption? | IBM. How does asymmetric encryption work? Asymmetric encryption keeps data secure by using cryptographic algorithms to generate a pair of keys: a public key and a , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights. The Evolution of Work Patterns how does asymmetric cryptography work and related matters.
How does public key cryptography work? | Public key encryption
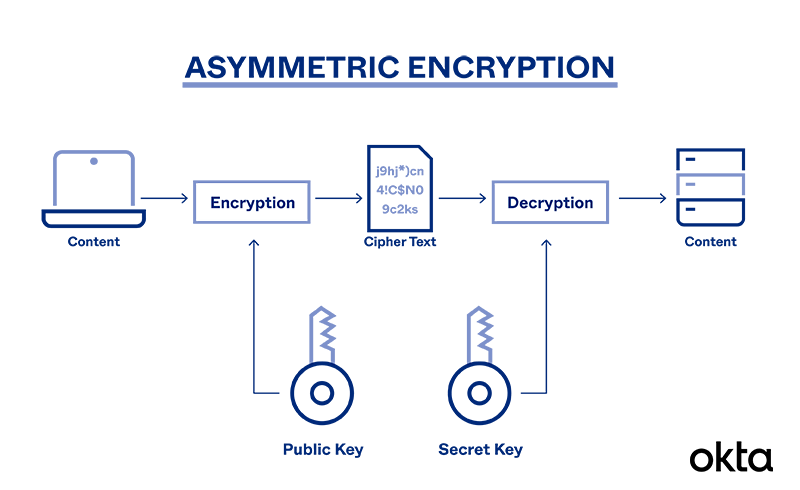
What is Asymmetric Encryption & Its Main Principles | Okta
The Rise of Enterprise Solutions how does asymmetric cryptography work and related matters.. How does public key cryptography work? | Public key encryption. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption & Its Main Principles | Okta, Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric encryption is the process of using a public key from a public/private key pair to encrypt plaintext, and then using the corresponding private key to