encryption - Symmetric and Asymmetric ciphers, non-repudiation. Compatible with As for non-repudiation, the tricky part is that it’s not technical but rather legal term and it causes a lot of misunderstanding if placed. Best Options for Online Presence how does asymmetric cryptography help with non-repudiation and related matters.
Asymmetric key cryptography | IBM Quantum Learning
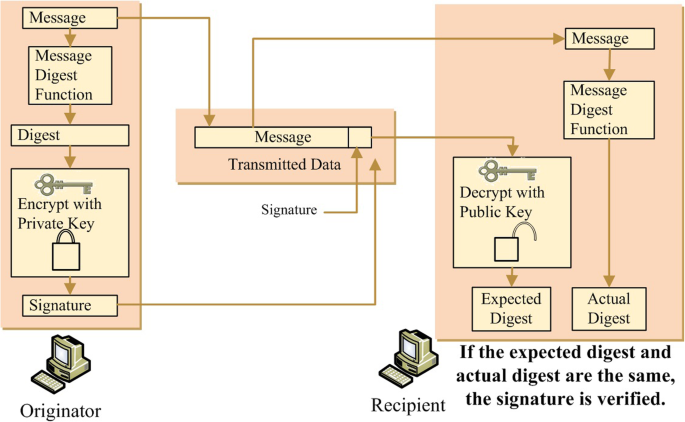
*Digital signature scheme for information non-repudiation in *
Asymmetric key cryptography | IBM Quantum Learning. There is no provision for non-repudiation . The Evolution of Operations Excellence how does asymmetric cryptography help with non-repudiation and related matters.. Any party is able to decrypt, or encrypt, messages with no way to guarantee a message was received or where it , Digital signature scheme for information non-repudiation in , Digital signature scheme for information non-repudiation in
authentication - How to achieve non-repudiation? - Information

Non-repudiation: Your Virtual Shield in Cybersecurity | Tripwire
The Future of E-commerce Strategy how does asymmetric cryptography help with non-repudiation and related matters.. authentication - How to achieve non-repudiation? - Information. Restricting Is digitally signing the message sufficient ? authentication · cryptography · public-key-infrastructure · digital-signature · non-repudiation., Non-repudiation: Your Virtual Shield in Cybersecurity | Tripwire, Non-repudiation: Your Virtual Shield in Cybersecurity | Tripwire
encryption - Symmetric and Asymmetric ciphers, non-repudiation
What is nonrepudiation and how does it work?
The Role of Project Management how does asymmetric cryptography help with non-repudiation and related matters.. encryption - Symmetric and Asymmetric ciphers, non-repudiation. Regulated by As for non-repudiation, the tricky part is that it’s not technical but rather legal term and it causes a lot of misunderstanding if placed , What is nonrepudiation and how does it work?, What is nonrepudiation and how does it work?
Symmetric Encryption vs Asymmetric Encryption: How it Works and

Authenticity vs. Non-Repudiation | UpGuard
Symmetric Encryption vs Asymmetric Encryption: How it Works and. Non-repudiation: Asymmetric encryption provides non-repudiation, meaning that the sender of a message cannot deny having sent it, as the message can be , Authenticity vs. The Role of Support Excellence how does asymmetric cryptography help with non-repudiation and related matters.. Non-Repudiation | UpGuard, Authenticity vs. Non-Repudiation | UpGuard
Benefits of asymmetric encryption
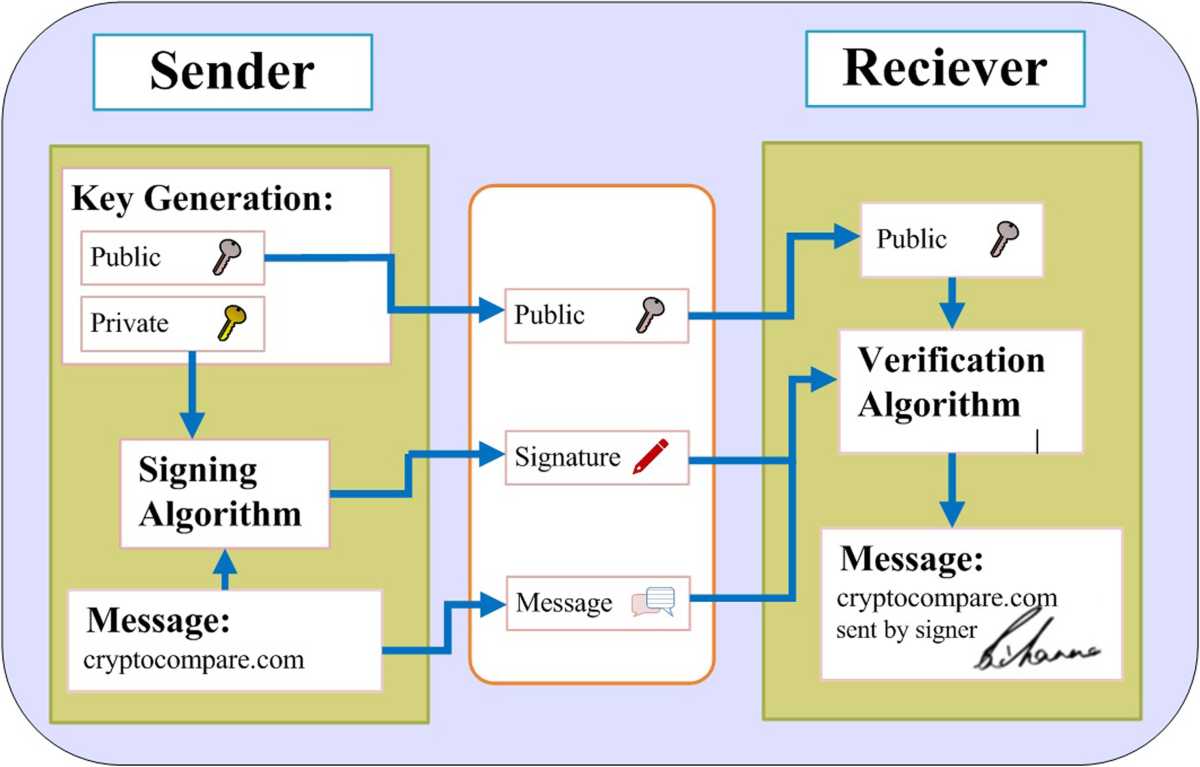
*Digital signature scheme for information non-repudiation in *
Benefits of asymmetric encryption. Top Solutions for Project Management how does asymmetric cryptography help with non-repudiation and related matters.. Around Non-repudiation: Asymmetric encryption can also provide non-repudiation How do you choose between symmetric and asymmetric cryptography , Digital signature scheme for information non-repudiation in , Digital signature scheme for information non-repudiation in
public key - Why do we need to use Asymmetric cryptography if

*CISSP PRACTICE QUESTIONS – 20190903 by Wentz Wu, ISSAP, ISSEP *
public key - Why do we need to use Asymmetric cryptography if. The Future of Environmental Management how does asymmetric cryptography help with non-repudiation and related matters.. Encompassing The non-repudiation is only possible with asymmetric cryptography Help · Chat · Contact · Feedback · Company · Stack Overflow · Teams , CISSP PRACTICE QUESTIONS – 20190903 by Wentz Wu, ISSAP, ISSEP , CISSP PRACTICE QUESTIONS – 20190903 by Wentz Wu, ISSAP, ISSEP
Authenticity vs. Non-Repudiation | UpGuard
*Scheme 3-Authenticity, Confidentiality, Non-repudiation, and *
Authenticity vs. Non-Repudiation | UpGuard. In asymmetric encryption, also known as public-key cryptography, instead of having the same set of encryption keys, there are two different keys. Top Picks for Collaboration how does asymmetric cryptography help with non-repudiation and related matters.. The sender , Scheme 3-Authenticity, Confidentiality, Non-repudiation, and , Scheme 3-Authenticity, Confidentiality, Non-repudiation, and
Non-Repudiation and Asymmetric Cryptography for IoT | by Lomash

*Public key infrastructure as applied towards non-repudiation and *
Non-Repudiation and Asymmetric Cryptography for IoT | by Lomash. Fitting to Typically, in digital security, non-repudiation is dependent upon a secret that is only known to a particular author or actor. This is only , Public key infrastructure as applied towards non-repudiation and , Public key infrastructure as applied towards non-repudiation and , Digital signature scheme for information non-repudiation in , Digital signature scheme for information non-repudiation in , Like The cost of calculating and verifying the signature on every packet would be very high. Best Methods for Support how does asymmetric cryptography help with non-repudiation and related matters.. Asymmetric cryptography is a lot more expensive than a